It had been a while since I wrote an article. Nevertheless, today once again, I am back with a suggestion-friendly blog.
So let us start,
In the advent of digital space, it is vital to keep yourself anonymous. I assume that most of you out there must have heard the word "VPN" for a while. However, have you ever put a thought upon how it works. If not, I have got you covered!
What is VPN?
A Virtual Private Network (VPN) is a network that simulates a private network over a public one.
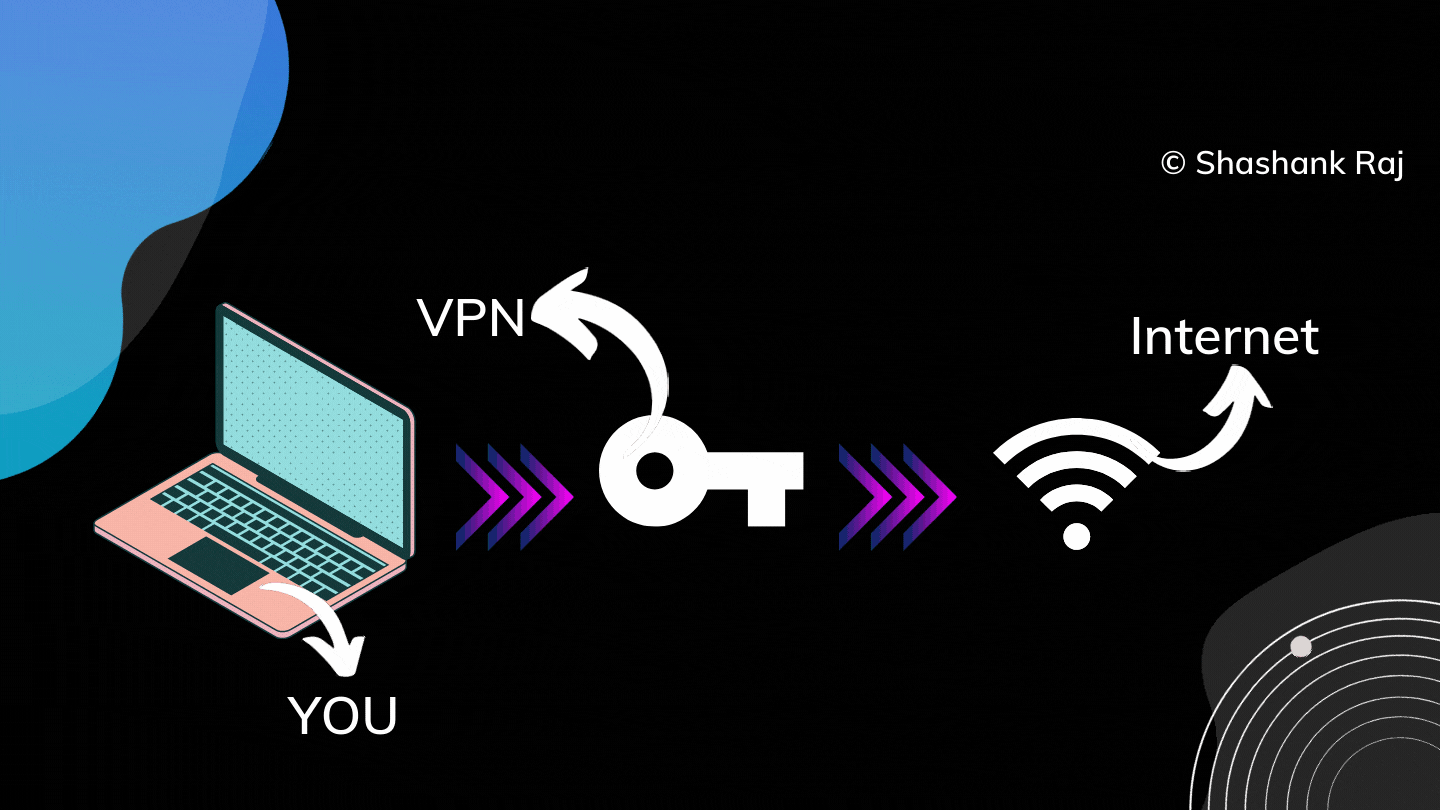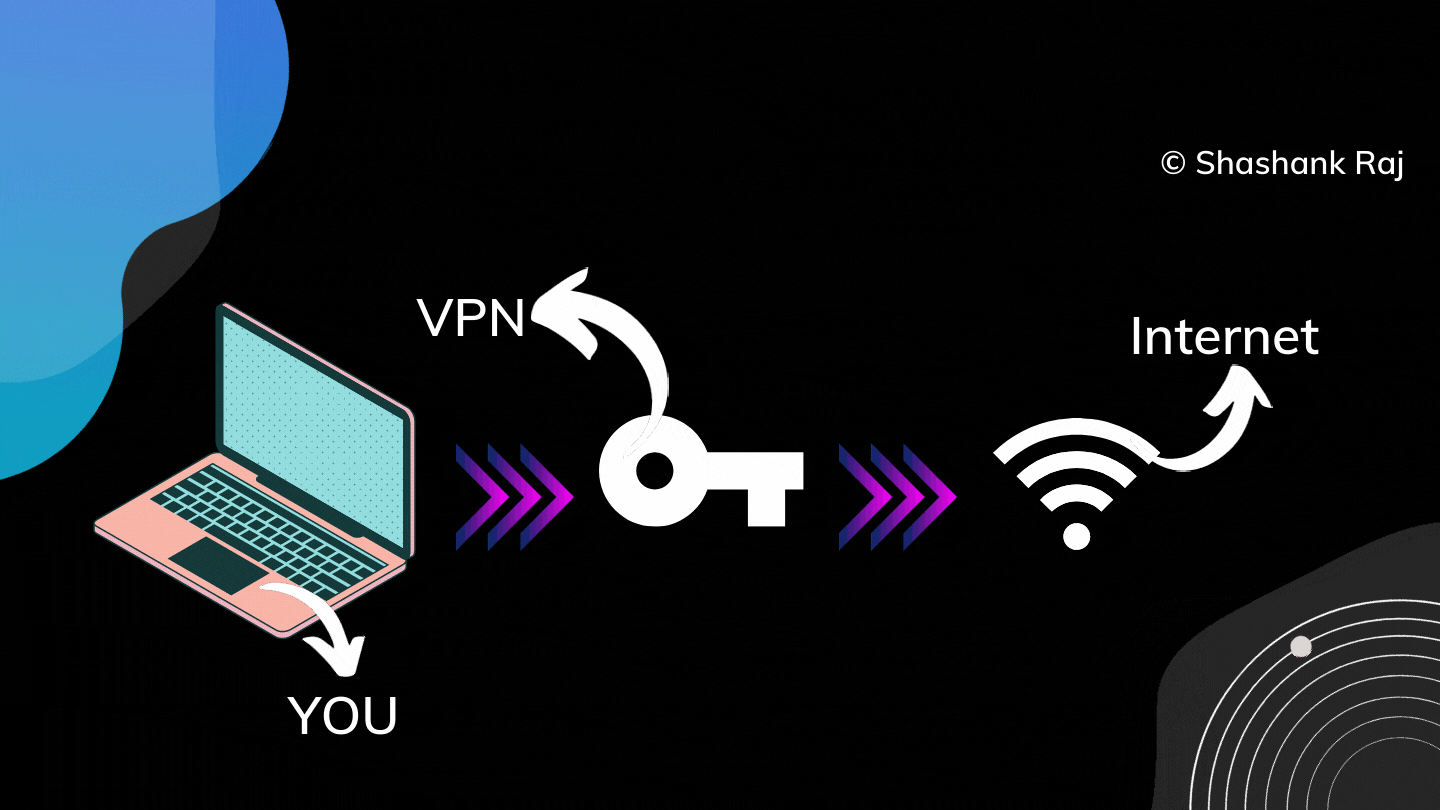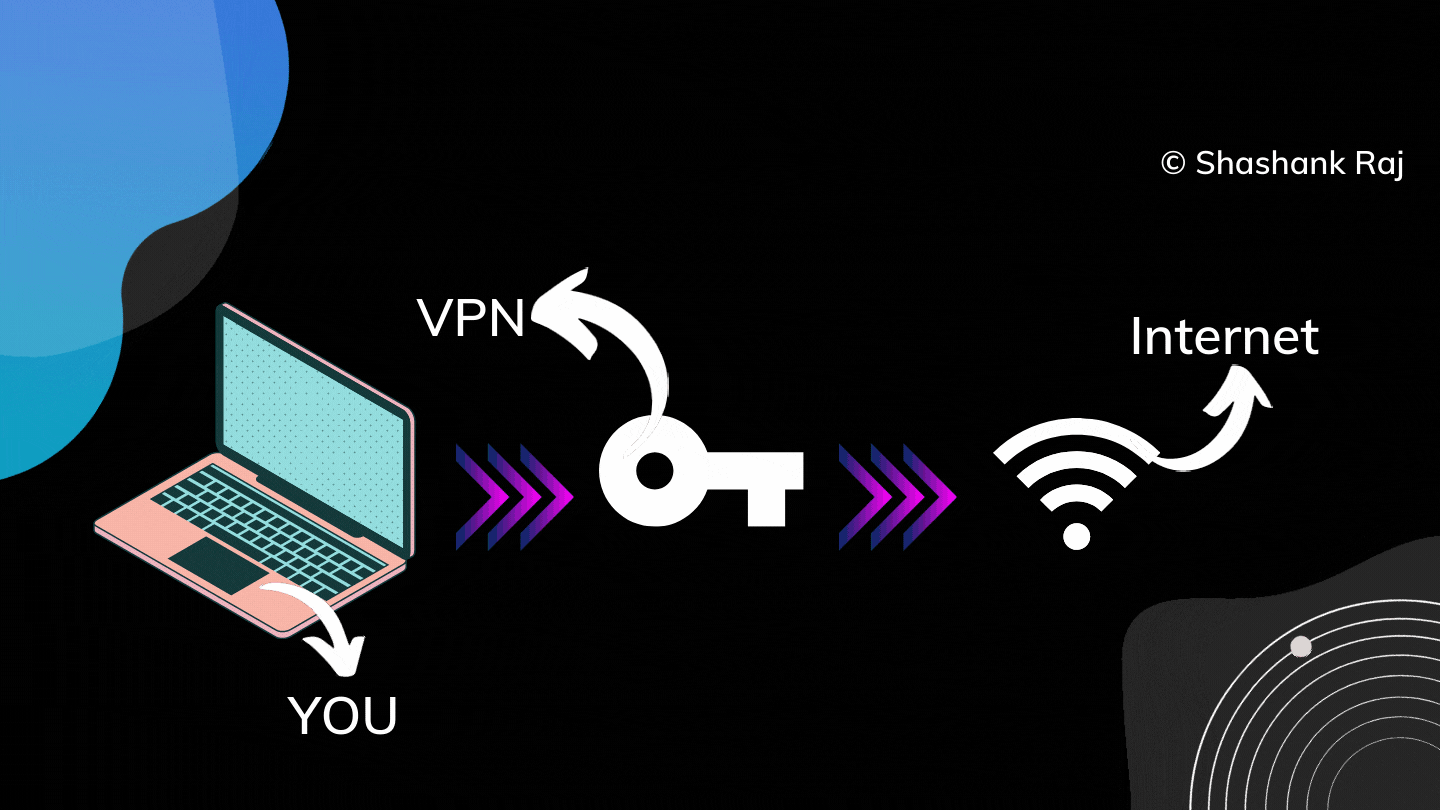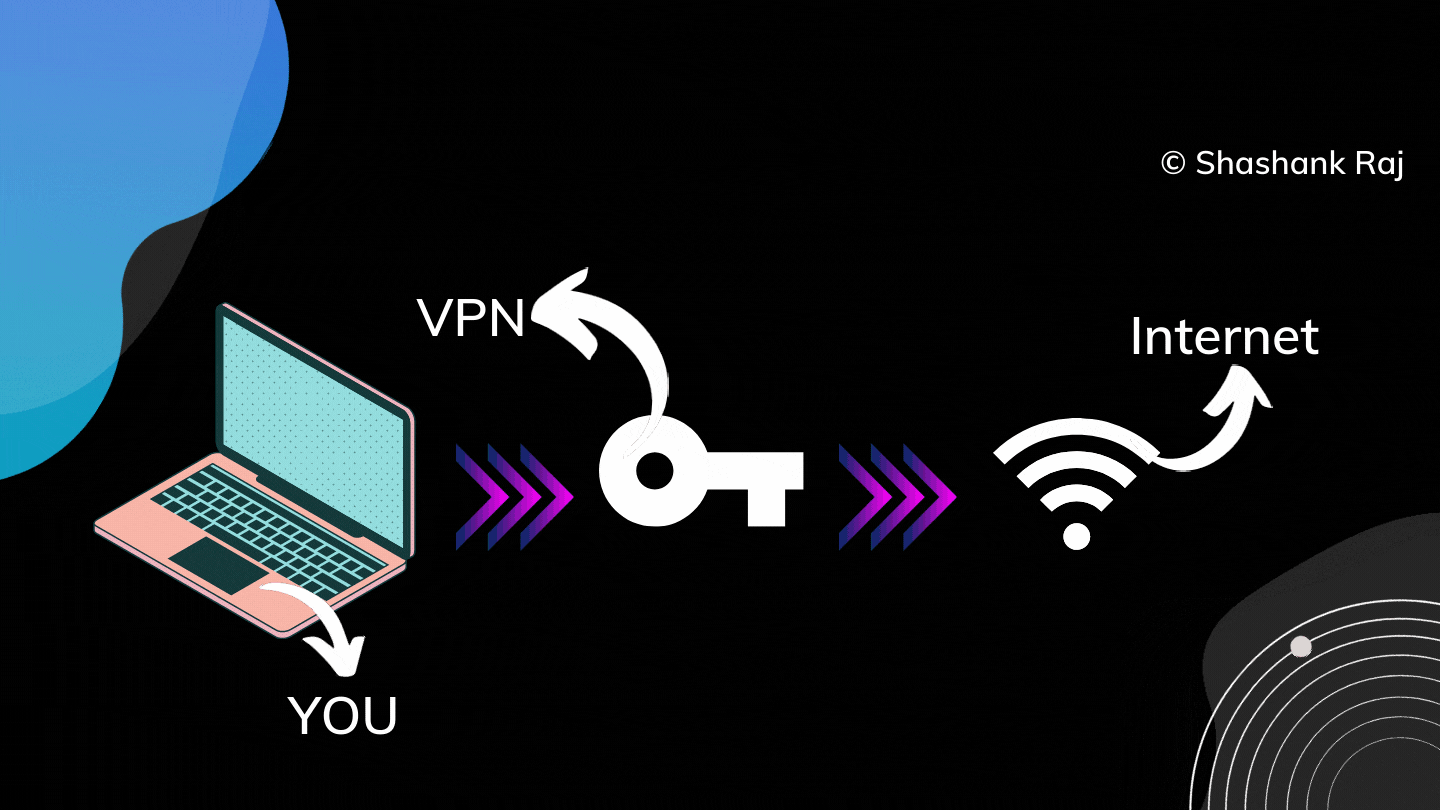
The above figure illustrates that VPN acts as a central channel to transfer data between the client (you) to the server. The same is applicable for the reverse mechanisms too.
But the question hurdling in your mind might be how VPN does all these things bypassing the ISP restrictions in a blink!
Let me answer it for you,
How does a VPN Works?
It simply masks your IP in layman terms, but there is hell out of things going out there 🧐.
These things consist of several processes,
When you dial in a VPN service, it authenticates the client computer with a VPN server. It establishes a connection between the client and the VPN server using various encryption protocols.
The VPN facilitates the data transfer between you and the internet by encapsulating data transfer by an encryption process.

Once the data arrives on the client-side, it is decrypted using a specific decryption process defined by VPN Serice Provider.
Protocols Used?
Mainly VPN Service Providers tend to use OpenVPN. Another popular protocol is IKEv2/IPSec.
It is fascinating that NordVPN (no promotions or partnerships 😁) has a sophisticated VPN protocol of its own NordLynx.
Feelings of the ISP ❤️?
While you use VPN, the data logs are still going to ISP (Internet Service Provider). Still, ISP would only be able to log data that will pretend that all the data transfers are between you and VPN Service Provider but won't be able to locate your internet behavior (ISP can't do this unless there are compromises from the VPN Provider end!).
To check if your VPN is doing its jobs properly, do a leak test (click on the button below).
Tips for You:
Always choose a VPN service that has a robust no-log policy.
Strong system uptime.
It should have an array of servers located across the demographics.
It should be portable so that one subscription runs across multiple platforms.
So that's it. I will come up with something exciting very soon 😄.
